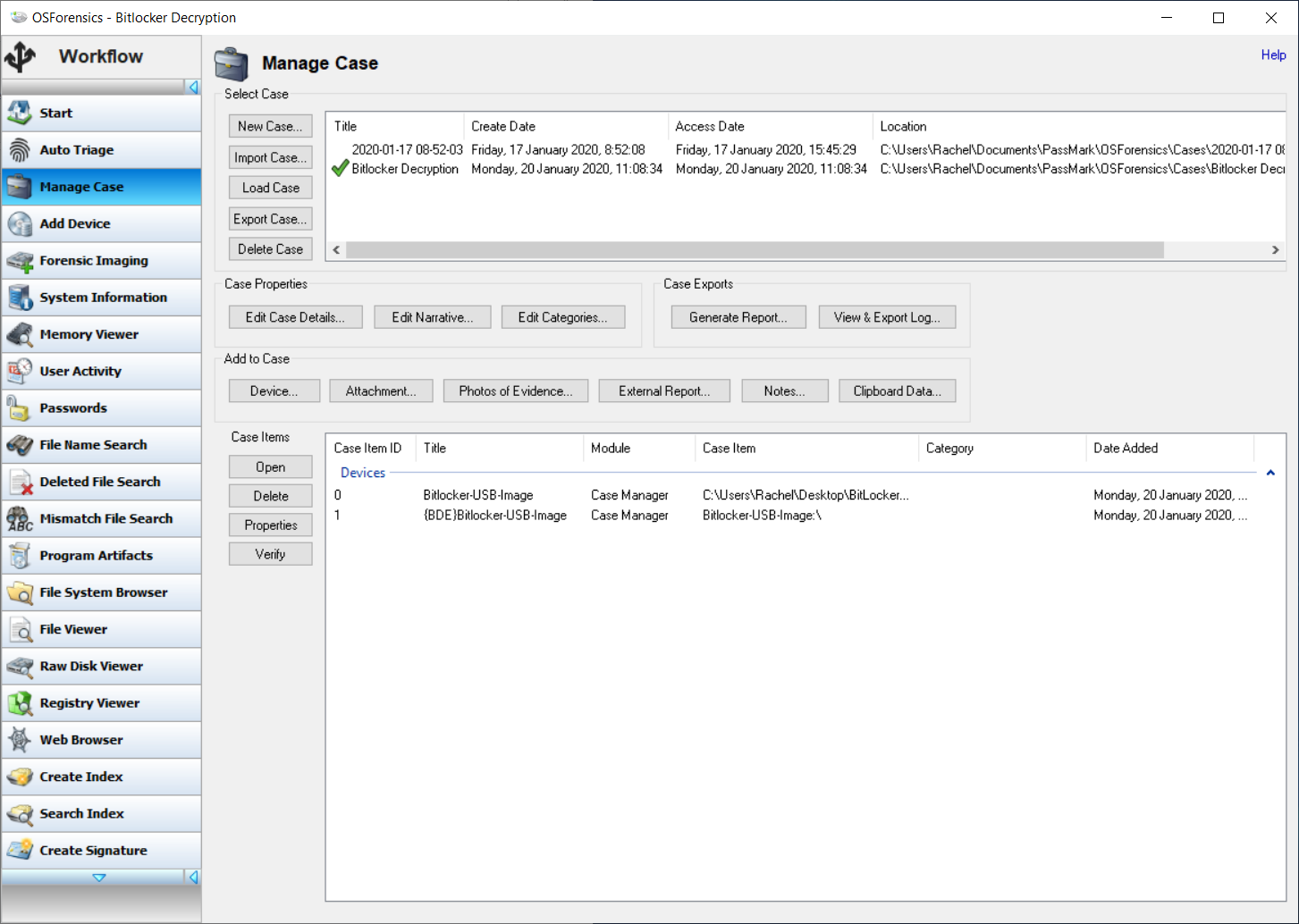
Bitlocker Decryption Time . Put this in a bat file and run it. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Leave it running in a command terminal.
from www.osforensics.com
Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Put this in a bat file and run it. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Leave it running in a command terminal. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage.
OSForensics FAQs How to Decrypt a BitLocker Drive
Bitlocker Decryption Time You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Put this in a bat file and run it. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Leave it running in a command terminal. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times.
From support.kaspersky.com
Starting BitLocker Drive Encryption Bitlocker Decryption Time Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Leave it running in a command terminal. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of. Bitlocker Decryption Time.
From notebooks.com
How to Encrypt Your Hard Drive With BitLocker Bitlocker Decryption Time Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Leave it running in a command terminal. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on. Bitlocker Decryption Time.
From www.easyuefi.com
How to decrypt BitLocker encrypted drive in macOS & Mac OS X? Bitlocker Decryption Time Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Leave. Bitlocker Decryption Time.
From suamaytinhbinhdan.blogspot.com
Hướng dẫn Các chỉ dẫn Tắt BitLocker Trong Win 10 Bitlocker Decryption Time Leave it running in a command terminal. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Its been over 36 hours and my drive (~480gb) is still undergoing decryption. Bitlocker Decryption Time.
From developingdaily.com
How To Disable BitLocker in Windows 10? Developing Daily Bitlocker Decryption Time Leave it running in a command terminal. Put this in a bat file and run it. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. You can use bitlocker to mitigate unauthorized. Bitlocker Decryption Time.
From www.onurcan.com.tr
Bitlocker to go Encryption Decryption Virtualization Blog Bitlocker Decryption Time You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Put this in a bat file and run it. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Decryption key that can be used with the bitlocker repair tool to. Bitlocker Decryption Time.
From www.easyuefi.com
How to decrypt BitLocker encrypted drive in macOS & Mac OS X? Bitlocker Decryption Time Put this in a bat file and run it. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Leave it running in a command terminal. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Its been over 36. Bitlocker Decryption Time.
From developingdaily.com
How To Remove BitLocker From USB? Developing Daily Bitlocker Decryption Time Put this in a bat file and run it. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Leave it running in a command terminal. Although bitlocker encryption occurs in. Bitlocker Decryption Time.
From www.stellarinfo.co.in
[Solution]How to recover data from BitLocker encrypted hard drive? Bitlocker Decryption Time Leave it running in a command terminal. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers. Bitlocker Decryption Time.
From www.softpedia.com
Download M3 BitLocker Decryption Bitlocker Decryption Time Put this in a bat file and run it. Leave it running in a command terminal. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Although bitlocker encryption occurs in the background. Bitlocker Decryption Time.
From www.itechtics.com
How To Manage BitLocker Using Command Line In Windows (Managebde) Bitlocker Decryption Time Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Leave it running in a command terminal. Put this in a bat file and run it. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Its been over 36. Bitlocker Decryption Time.
From www.osforensics.com
OSForensics FAQs How to Decrypt a BitLocker Drive Bitlocker Decryption Time Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Leave it running in a command terminal. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Although bitlocker encryption occurs in the background while a user continues to work with. Bitlocker Decryption Time.
From recoverit.wondershare.com
BitLocker Stuck Encrypting or Decrypting 8 Proven Fixes Bitlocker Decryption Time Put this in a bat file and run it. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Decryption key that can be used with the bitlocker repair tool to reconstruct critical. Bitlocker Decryption Time.
From notebooks.com
How to Encrypt Your Hard Drive With BitLocker Bitlocker Decryption Time Leave it running in a command terminal. Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Although bitlocker encryption occurs in the background while a user continues to work with the system. Bitlocker Decryption Time.
From www.forensicfocus.com
BitLocker Decryption Explained Forensic Focus Bitlocker Decryption Time Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts of a drive and salvage. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Put. Bitlocker Decryption Time.
From help.ubuntu.com
Windows will now inform you that it is going to decrypt the data. Bitlocker Decryption Time Its been over 36 hours and my drive (~480gb) is still undergoing decryption on the black screen. Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Put this in a bat file and run it. Decryption key that can be used with the bitlocker repair tool to reconstruct critical parts. Bitlocker Decryption Time.
From www.sexiezpix.com
Your Guide To Using Bitlocker Encryption On Windows Solveyourtech Bitlocker Decryption Time Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. You can use bitlocker to mitigate unauthorized data access on lost or stolen computers by encrypting all user files and. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. Its. Bitlocker Decryption Time.
From www.youtube.com
How to Remove Bitlocker Encryption In Windows 10 Turn Off Bitlocker Bitlocker Decryption Time Although bitlocker encryption occurs in the background while you continue to work, and the system remains usable, encryption times. Put this in a bat file and run it. Although bitlocker encryption occurs in the background while a user continues to work with the system remaining usable, encryption times. You can use bitlocker to mitigate unauthorized data access on lost or. Bitlocker Decryption Time.